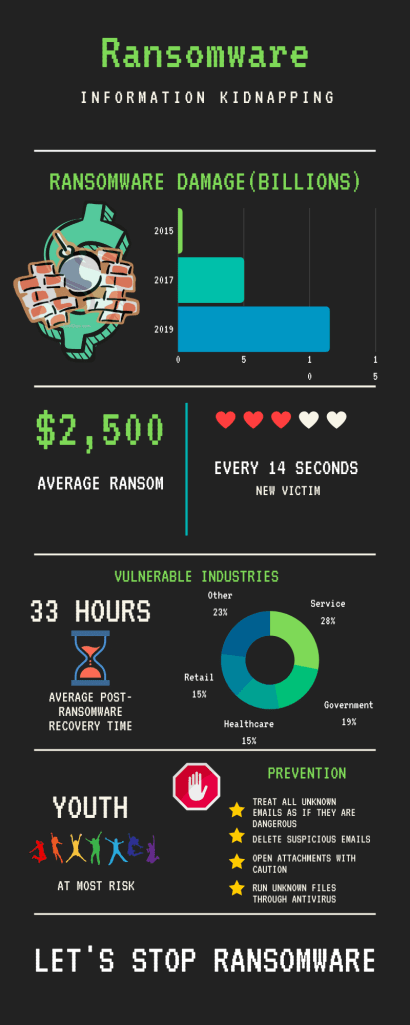
In my previous series blog post, I introduced identity theft and explained its growing impact on people around the world. With your personal, digital, financial, and medical identity at stake, you should be worried about the possibilities of getting your identity stolen. Because the Identity Theft Resource Center warns that identity theft could result from data breaches and personal negligence at the very least, no single solution is capable of solving all forms of identity theft. However, as Verizon suggests in its 2019 Data Breach Investigation report, passwords play a large role in both the cause and aftermath of identity theft. Considering that a weak password allows a hacker to access a “protected” database and gain access to what is most like going to be usernames and passwords, passwords as a whole should not be overlooked.
As suggested, passwords play a large role in identity theft. Thus, while you and I might feel tempted to solely blame and hold companies liable for managing our data, they are not entirely to blame. To Robert Siciliano, a security analyst and CEO of Safr.me, argues that we could take better precautions at being wiser with our passwords. Siciliano and many other experts agree that many people don’t take their passwords seriously and set them common passwords like “password” and “123456”. Instead, Siciliano argues people to include “uppercase, lowercase, numbers, and characters” as well as “ change them up frequently”. Create a more complex password will diminish the possibility of a hacker trying to brute force popular sites with common passwords using stolen email addresses. While I most certainly agree with Siciliano, what he fails to mention is why people should do so. Not providing such an answer could deter some from fulfilling such steps as they don’t understand what is the point.
Because it is most certainly true that a data breach would provide a hacker with the email, username, and password of your account for that service, I argue that by changing passwords for each digital account, you would be safer. In my perspective, if you go with the same password for every account, a hacker would essentially brute force your credentials on the most common online services and gain access to all of them. Therefore, to limit the impact of a single breach, one should use a completely different password for each account. In fact, while remembering a new password for each account might seem daunting, I suggest the use of password managers like 1Passowrd. Such services do all the storing and the generation of random and complicated passwords for you and make use of U.S. government employed encryption algorithms to store those random passwords safely.
Still, while a strong password won’t help much when in the hacker’s hands and switching passwords will only help in reducing the spread of a breach, one can add more layers of security to their accounts through additional authentication steps. Known as multi-factor authentication, these extra layers could take the form of SMS codes, emailed codes, and dedicated apps like Google Authenticator. All these methods work by providing a code that a login page requires in addition to credentials. Some experts approve of multi-factor authentication and argue for its widespread use due to its effectiveness. Take Troy Hunt, a security expert and CEO of Have I Been Pwned, suggests that one is able to use multi-factor authentication to better protect their accounts. As a result of those services, Hunt argues that “fewer accounts get compromised every time there’s a security breach.” Because a hacker essentially hits a login page requesting a code that they don’t have, they will be stopped before they are able to access the account. While to Hunt two-factor authentication works, I argue solely relying on it should be avoided.
As Verison puts it, “two-factor authentication is the spool pins in the lock” but it doesn’t necessarily mean that the lock cannot be broken. Take the case of email conformation. Should the hacker been able to access one’s email account using the same credentials as the ones they stole, using an emailed code as a security layer wouldn’t have been helpful. Siciliano would have agreed to such an example, allowing him to further prove the need to frequently change passwords among accounts. Even so, Kevin Mitnick, a former FBI most wanted hacker and now chief hacking officer at KnowBe4, also agrees with my point. Mitnick argues that a hacker who already knows your email could phish you into opening a website through a modified portal and unknowingly give them your two-factor authentication code. Thus, Mitnick suggests that even with the most advanced two-factor authentication, some social engineering could potentially bypass this security layer.
Regardless, my suggestion for protecting yourself from identity theft is to employ a combination of these methods. While it is proved that no method is perfectly capable of stopping a hacker from logging into your account and stealing your identity, by changing passwords for each account, using a password manager, and utilizing two-factor authentication, you would be capable of preventing unwanted digital access. Because not every hacker is a most wanted FBI hacker like Mitnick, a combination of these methods would be more than capable of stopping most hackers from doing more than attempting to use your stolen credentials. In the last few years of using a combination of these methods, I have yet to experience unwanted logins in any of my accounts. Therefore, as my solution has worked flawlessly for me saw far, I too believe that for you to follow such a strategy would help you in fending off identity theft.
Bibliography
Lane, Gina W., and Daniel Z. Sui. “Geographies of Identity Theft in the U.S.: Understanding Spatial and Demographic Patterns, 2002-2006.” GeoJournal, vol. 75, no. 1, 2010, pp. 43–55. JSTOR, http://www.jstor.org/stable/41148383. Accessed 4 Mar. 2020.
2019 Data Breach Investigations Report. Verison, 2019.
“Expert Interview with Robert Siciliano on Identity Theft.” Mint, 25 June 2014, http://www.mint.com/personal-finance-interviews/expert-interview-with-robert-siciliano-on-identity-theft.
“Identity Theft.” Consumer Information, 19 Feb. 2019, http://www.consumer.ftc.gov/articles/0005-identity-theft.
Long, Emily. “Common Habits That Put You at Risk for Identity Theft.” NBC News, 2018, http://www.nbcnews.com/better/business/6-common-habits-put-you-risk-identity-theft-ncna899251. Accessed 10 Mar. 2020.
Pascual, Al, et al. “2017 Identity Fraud: Securing the Connected Life.” Javelin, 1 Feb. 2017, http://www.javelinstrategy.com/coverage-area/2017-identity-fraud. Accessed 10 Mar. 2020.
Whittacker, Zack. “Cybersecurity 101: Two-Factor Authentication Can Save You from Hackers.” TechCrunch, 25 Dec. 2018, techcrunch.com/2018/12/25/cybersecurity-101-guide-two-factor/. Accessed 10 Mar. 2020.